Zero Trust Security Fundamentals for IT Professionals
Learn Zero Trust Fundamentals: NIST Architectural Model, Pillars, Design, Migration, Use Cases, Maturity Models & More
Zero Trust has evolved from an emerging concept to the preferred security strategy for enterprise networks, systems, applications, devices, data, and cloud services. Following high-profile breaches like SolarWinds and the U.S. federal government's mandate requiring Zero Trust adoption, organizations worldwide are rapidly implementing Zero Trust architectures.
Whether you're a cybersecurity professional, IT practitioner, security architect, or business leader, understanding Zero Trust fundamentals is now essential for modern security strategy and implementation.
This course teaches Zero Trust as a security strategy and framework, not just a collection of technologies. You'll learn the NIST-aligned architectural model and gain the shared vocabulary needed to collaborate with technical teams and business leaders.
This course provides vendor-neutral coverage of Zero Trust fundamentals, architecture, and implementation strategy. Perfect for beginners and experienced practitioners alike who need to understand Zero Trust beyond vendor marketing.
"This is a phenomenal class. I'm a professional trainer and consultant, and this instructor is top notch. He's got a great, calming voice which makes it easy to listen to. The material is technical, but he always makes sure it is understandable. I highly recommend this Zero Trust class for beginners to advanced students"
— Todd Lammle ⭐⭐⭐⭐⭐
"I am a long-time Cybersecurity veteran, but have not deployed a comprehensive ZTA. This course is very informative and easy to follow."
— Larry Mulloy ⭐⭐⭐⭐⭐
"I really enjoyed this class. Alton provided me with exactly what I was looking for, a solid overview of Zero Trust that went well beyond just a surface-level-understanding, without committing me to several days worth of training. Alton has a very comfortable and relatable teaching style, and his overall content organization, flow, use of impactful graphics, inclusion of additional Resources, and the key-concepts excerpts were all extremely helpful. Definitely one of the best online classes I've ever taken!"
— Brian Hillmar ⭐⭐⭐⭐⭐
"This course was excellent. It helped me move from zero to a place where I can confidently look for specific tools and vendors to help my organization become more secure."
— Michael Dewar ⭐⭐⭐⭐⭐
Welcome to the Course!
FREE PREVIEWQuick Course Overview
FREE PREVIEWWhy Learn Cyber Security from Me?
FREE PREVIEWDownload Course Lecture PDFs
Student Exercise: Introduce Yourself
Section Introduction
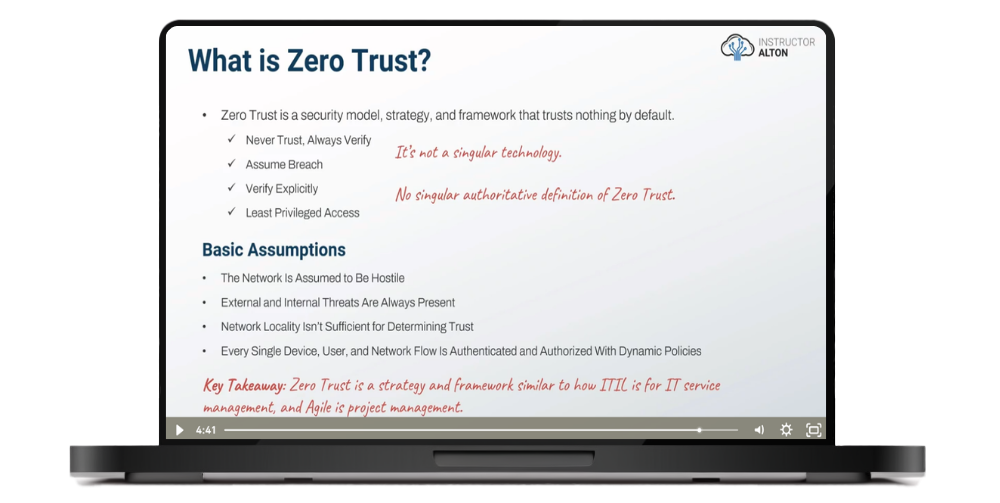
FREE PREVIEWWhat is Zero Trust?
FREE PREVIEWSome Zero Trust Definitions
FREE PREVIEWNever Trust, Always Verify
FREE PREVIEWZero Trust Enterprise
FREE PREVIEWTenets of Zero Trust
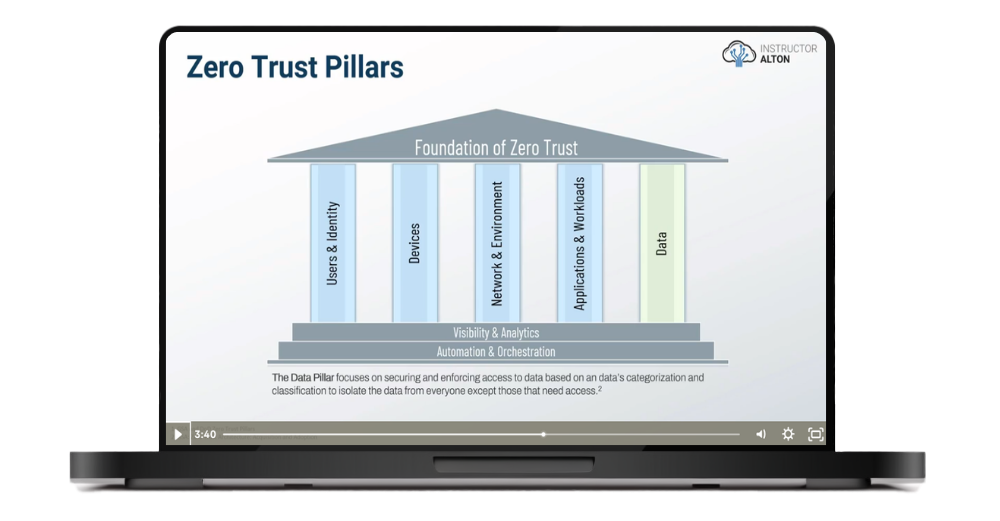
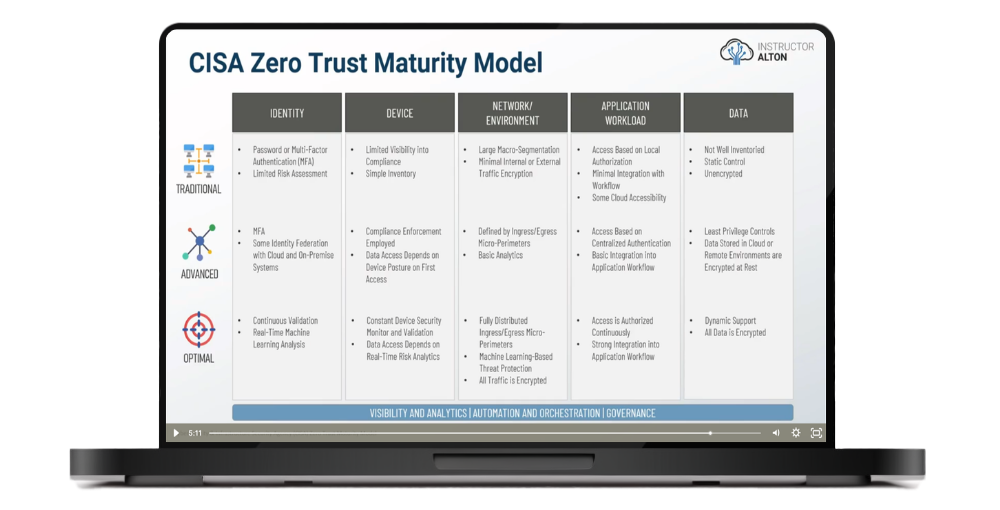
Zero Trust Pillars
Zero Trust Historical Context
A Glimpse into ZTA
Section Quiz
Section Introduction
Why Do We Need Zero Trust?
Perimeter Security Pitfalls
Digital Transformation
Microsoft Case Study
The State of Zero Trust
Case Study: From SolarWinds to Zero Trust
Section Quiz
Section Introduction
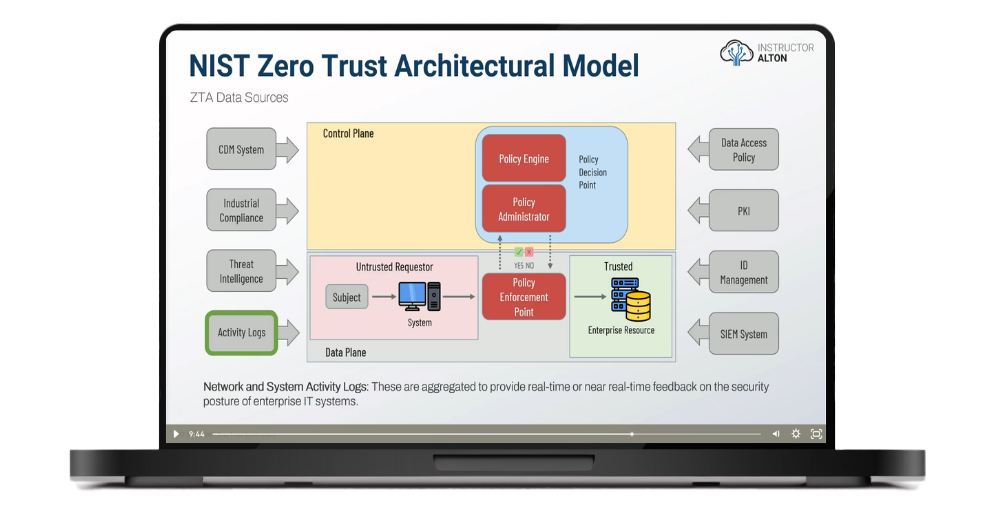
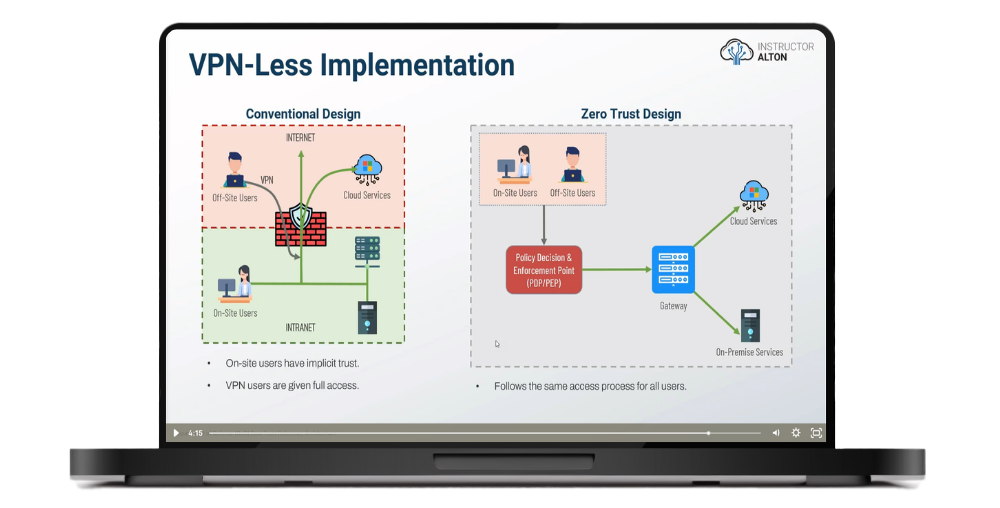
The NIST Zero Trust Architectural (ZTA) Model
Example Real-Life ZTA Solutions
NIST ZTA Architecture Approaches
NIST ZTA Deployment Models
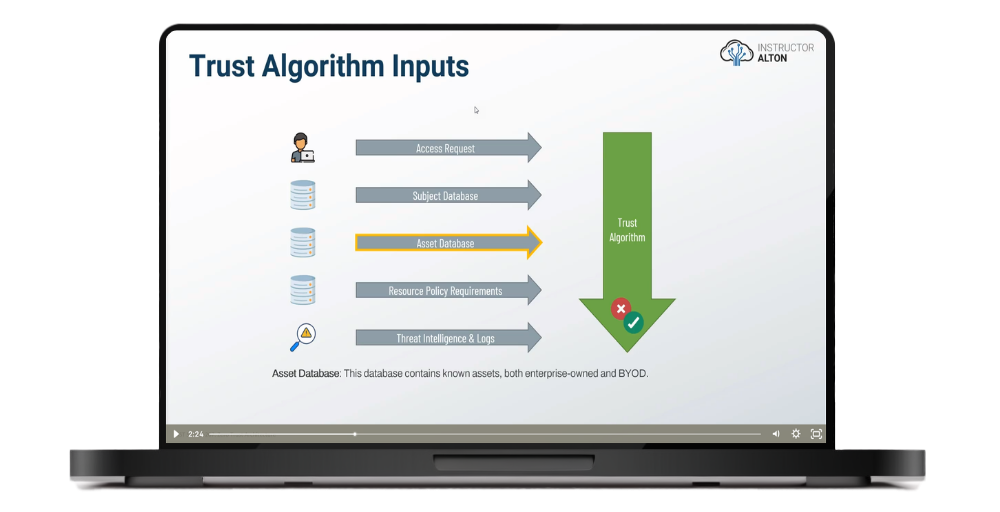
Introduction to Trust Algorithms & Policies
Section Quiz
Section Introduction
Reviewing the Pillars of Zero Trust
Securing the Users & Identity Pillar
Securing the Devices Pillar
Securing the Network & Environment PIllar
Securing the Applications & Workloads Pillar
Securing the Data Pillar
Foundational Components
Bringing It All Together
Case Study: Colonial Pipeline Cyber Attack
Section Quiz
Section Introduction
There is No Right Way to Zero Trust
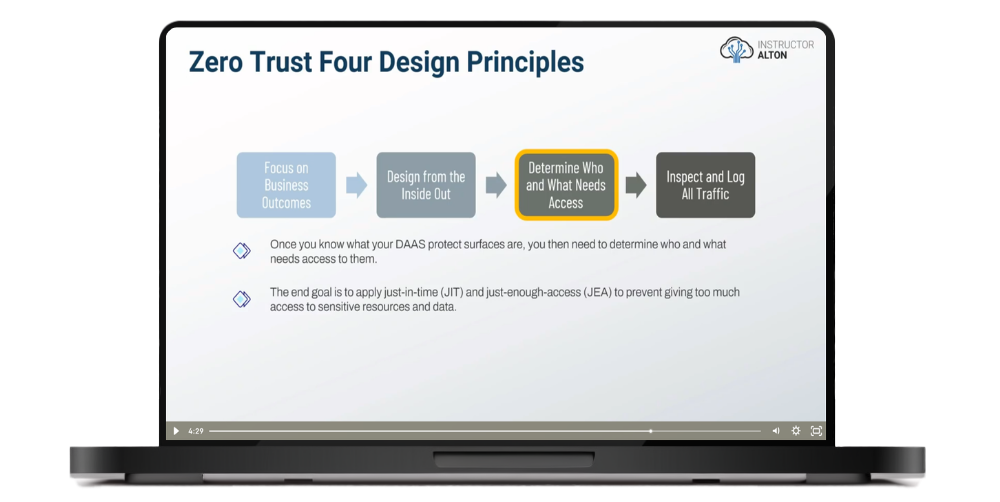
Zero Trust Design Principles
The Five-Step Zero Trust Design Methodology
Forrester’s Five Steps to Zero Trust
Section Quiz

Alton is the founder of Alton Teaches LLC and a former college professor. He spent 12 years as a cybersecurity specialist at the U.S. Department of Treasury working in governance, risk, and compliance. He holds an MBA in Information Assurance and Security Management and multiple certifications including CISSP, Security+, Network+, and Forrester Certified: Adopting Zero Trust.
250,000+ students taught across cybersecurity and IT courses. 90,000+ copies sold of his bestselling books.
This course focuses on Zero Trust as a security strategy and framework, not just a collection of vendor products. You'll understand the conceptual architecture that can be implemented across any technology stack.
Join 250,000+ students learning modern cybersecurity strategies. NIST-aligned training, lifetime access, 14-day money-back guarantee.
This course is designed for IT professionals, cybersecurity practitioners, security architects, network engineers, cloud professionals, and business/technology leaders involved in Zero Trust strategy, architecture, or implementation. It's valuable for both beginners new to Zero Trust and experienced practitioners seeking structured, vendor-neutral knowledge.
No. This course teaches Zero Trust as a security strategy and conceptual architectural framework. You won't configure firewalls, SIEM systems, or other security devices. Instead, you'll gain the strategic understanding needed to guide Zero Trust initiatives, make informed decisions, and collaborate effectively with technical teams.
No. This course starts with fundamentals and builds systematically. You should have basic IT and cybersecurity knowledge, but no prior Zero Trust experience is required. Familiarity with basic network concepts is helpful but not mandatory.
The course contains 4 hours of video content across 10 sections. Most students complete it within one to two weeks, but you have lifetime access so you can learn at your own pace.
You get 4 hours of video lectures mapped to NIST SP 800-207, 8 section quizzes, analysis of real-world case studies (SolarWinds, Colonial Pipeline), coverage of multiple maturity models (NSA, Microsoft, CISA, DoD), downloadable PDF versions of all slides, and lifetime access to all materials.
Yes. This course teaches the NIST Zero Trust architectural model and conceptual frameworks applicable to any technology stack. While we examine real-world examples from Microsoft, Cloudflare, and others, the focus is on universal principles and strategies, not vendor-specific products.
Yes. You'll learn design methodologies, migration strategies, how to build a business case, create Zero Trust teams, leverage maturity models, and apply practical use cases. This course provides the strategic foundation needed to guide Zero Trust initiatives effectively.
We offer a 100% satisfaction guarantee. If you are unsatisfied with your purchase, you may request a refund within 14 days of the original purchase date.