Risk Management 101 for IT Professionals: Essential Concepts
Learn the Fundamentals of Risk Management for IT and Cybersecurity Professionals
Most business executives recognize that uncertainties in the business environment are leading to increasingly complex risks, yet only one-third of organizations have mature risk management processes in place. The global financial cost of cyber attacks has exceeded $10.5 trillion in 2025 and continues to grow as threats become more sophisticated.
Whether you're an aspiring IT professional, experienced technician, or cybersecurity specialist, understanding risk management is essential. Risk management is embedded in everything we do in IT—from network security to project planning to compliance.
This course is based on real-world experience, not just theory. You'll learn IT risk management fundamentals through practical explanations, real business case studies, and actionable frameworks you can apply immediately.
This course provides comprehensive coverage of IT risk management essentials, from understanding what risk really means to implementing effective monitoring and control processes. Perfect for IT professionals at any level.
"I enjoyed this course! This was a great Risk Assessment refresher course for me. I like how the content is structured to make the information clear and easy to grasp. The practical explanations and examples bring the concepts home. I also like the expanded definitions which gives you a better idea of what the terminology entails. I found the case studies insightful. If you want to get a grip on the essential concepts of IT Risk Management, I recommend this course!"
— Surette Kimble ⭐⭐⭐⭐⭐
"As with all of Alton's courses here on Udemy - his instruction is perfectly paced and structured in a way that students of all levels can be engaged and understand the material. Risk management is a topic that is coming up more and more in real world scenarios and Alton's course is a great entry point into this expanding field. Thanks Alton and keep the great content coming!!!!"
— Kevin Frenette ⭐⭐⭐⭐⭐
"I had a great learning experience with this course. The instructor did a fabulous job of structuring the concepts in such a way that they build on each other. The lectures flowed and were easy to assimilate. 5 stars!"
— Isaac Paul ⭐⭐⭐⭐⭐
Welcome to the Course
FREE PREVIEWWhy Learn IT Risk Management from Me?
FREE PREVIEWCourse Lecture PDFs
Section Introduction
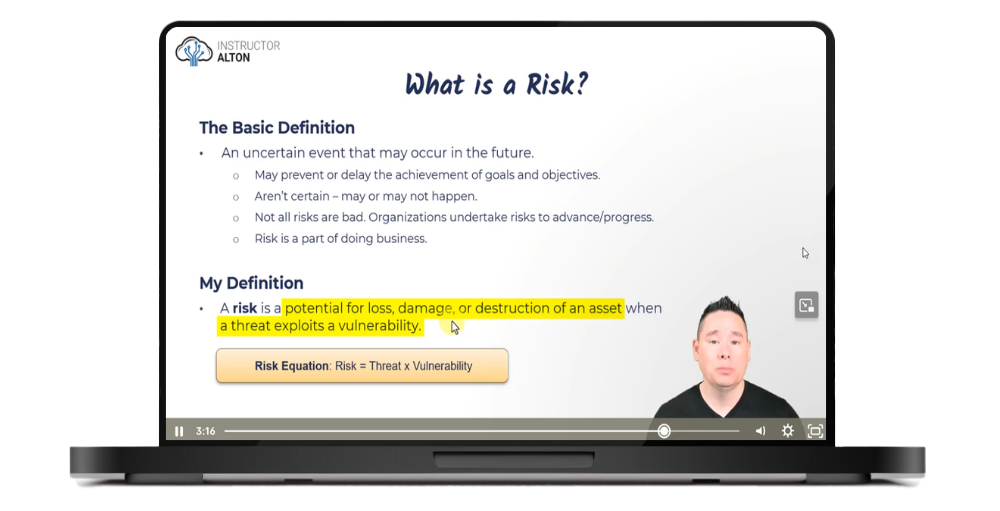
FREE PREVIEWWhat is a Risk?
FREE PREVIEWWhat is an Issue?
FREE PREVIEWWhat is Risk Management?
FREE PREVIEWWho Uses Risk Management?
The Elements of Risk
Assets, Threats, Vulnerabilities and Risks
Tangible and Intangible Assets
The Three Categories of Threats
Common IT Vulnerabilities
Risk Categories
The Risk Management Lifecycle
Understanding Risk Section Quiz
Section Introduction
Why do We Need Risk Management?
Legal and Regulatory Concerns
Deeper Dive Look at IT Vulnerabilities
The Evolving Cybersecurity Landscape 2024
Colonial Pipeline Case Study
Student Exercise: Colonial Pipeline Case Study Analysis
Section Introduction
The Role of Risk Appetite and Tolerance
Identifying IT Risks
IT Security Assessments
SWOT Analysis Case Study: Cloud Computing
Understanding Risk Interdependencies
Netflix Case Study: Calculated Risk for Cloud Success
Student Exercise: Netflix Case Study Analysis
Risk Identification Section Quiz
Section Introduction
Types of Risk Assessments
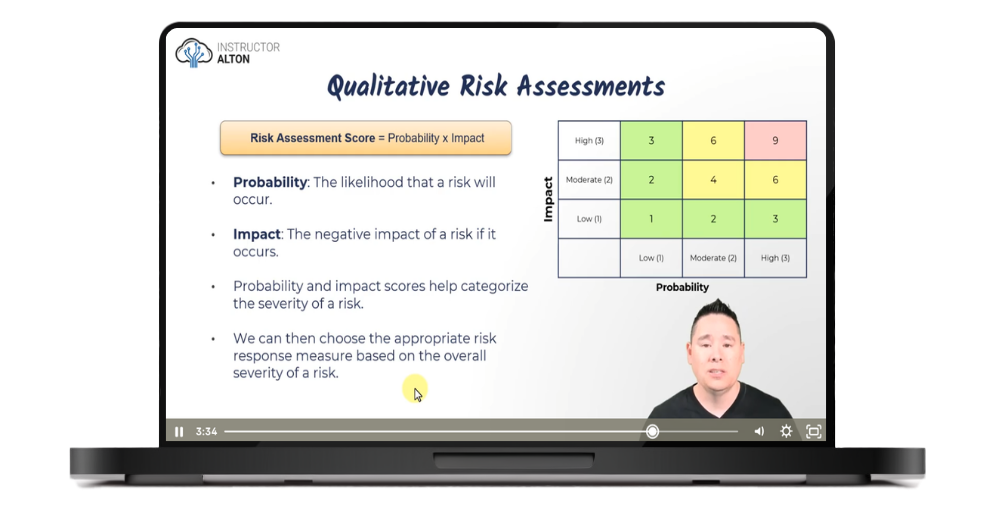
Qualitative Risk Assessments
Quantitative Risk Assessments
Sample Risk Assessments
Risk Assessments Section Quiz
Section Introduction
The Four Risk Response Categories
Risk Avoidance and Acceptance
Risk Mitigation and Transference
Understanding Security Controls
Combined Risk Response Activities
Understanding Residual Risk
OVHcloud Case Study: The Fire that Tested the Cloud
Student Exercise: OVHcloud Case Study Analysis
Risk Responses and Controls Section Quiz

Alton is the founder of Alton Teaches LLC and a former college professor. He spent 12 years as a cybersecurity specialist at the U.S. Department of the Treasury, working in governance, risk, and compliance, where risk management was a daily responsibility. He holds an MBA in Information Assurance and Security Management and multiple certifications, including CISSP, Security+, and Network+.
250,000+ students taught across cybersecurity and IT courses. 90,000+ copies sold of his bestselling books.
This course is built on years of hands-on risk management experience in government cybersecurity operations. You'll learn the frameworks and methodologies that actually work in real IT departments, not just academic theory.
Join 250,000+ students building essential IT skills. Lifetime access, 14-day money-back guarantee.
This course is designed for aspiring and experienced IT professionals, cybersecurity specialists, and anyone working in technology who needs to understand risk management. It's perfect for those who want to advance their careers by adding critical risk management skills to their toolkit.
No. This is an entry-level course designed to teach you risk management fundamentals from scratch. You only need a basic understanding of information technology to get started.
The course contains 3 hours of video content across 10 sections. Most students complete it within one week, but you have lifetime access so you can learn at your own pace.
You get 3 hours of video lectures, 5 section quizzes to test your knowledge, analysis of real-world case studies including the Colonial Pipeline attack, downloadable PDF versions of all slides, and lifetime access to all materials.
Yes, this covers technical IT risk management concepts—but it's designed to be accessible. Everything is explained clearly with practical examples. If you work in IT or cybersecurity, you'll understand the material.
We offer a 100% satisfaction guarantee. If you are unsatisfied with your purchase, you may request a refund within 14 days of the original purchase date.