Information Security Management Fundamentals for Non-Techies
Learn Information Security, Risk Management, Incident Response, Compliance, Network Security Fundamentals & More
Cyber threats are more advanced and relentless than ever. In 2024, ransomware attacks surged by 84%, phishing incidents exploded by over 1,200%, and the average cost of a data breach jumped to $4.88 million—the largest single-year increase since the COVID pandemic. Organizations are taking an average of 258 days just to detect and contain a breach.
Whether you're a business owner, aspiring IT professional, or someone looking to understand how cybersecurity really works, this comprehensive course gives you the essential foundation you need to protect your organization and advance your career.
This isn't just a series of lectures—it's a comprehensive educational program designed specifically for non-technical professionals who need to understand information security management.
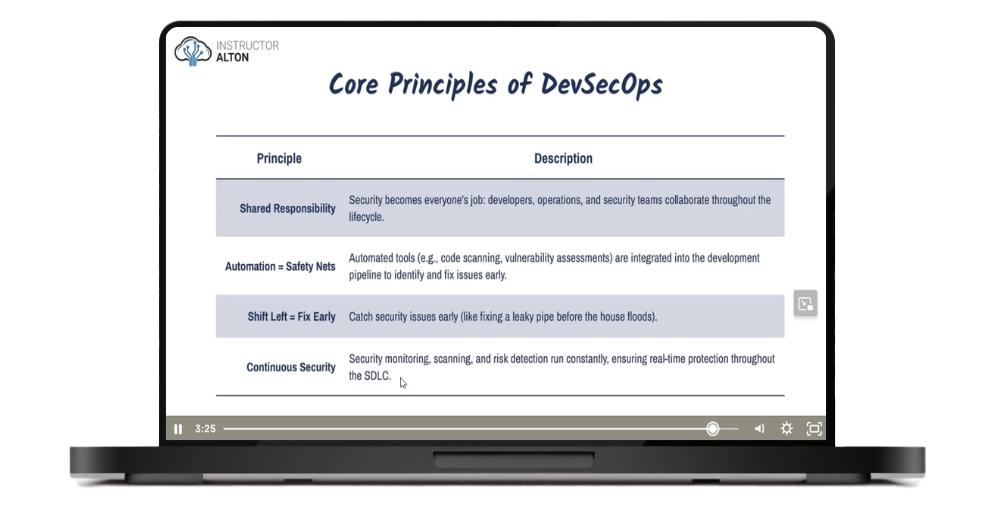
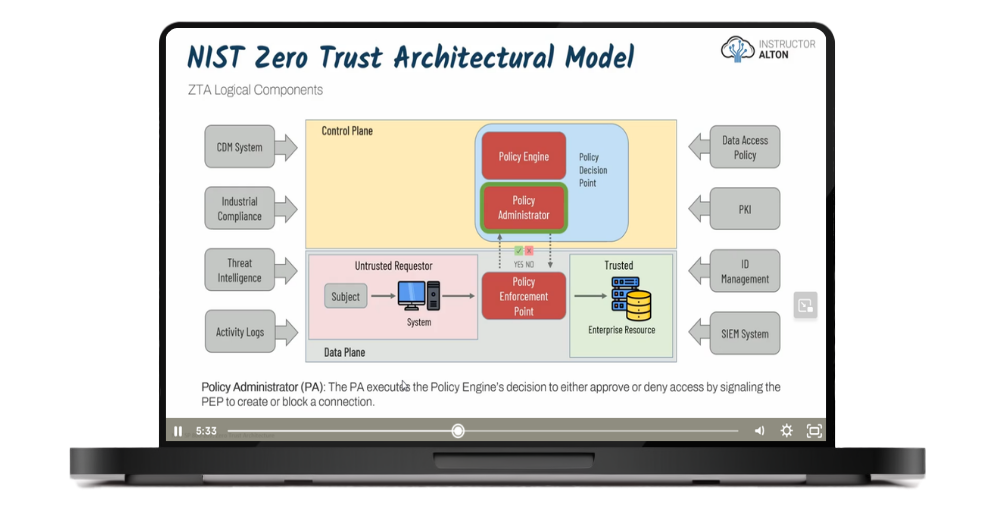
This course provides a complete, high-level overview of information security management—designed specifically for beginners and non-technical professionals. You'll gain a solid understanding of how cybersecurity works in real organizations, from risk management and compliance to incident response and Zero Trust architecture.

"As someone without a technical background, I found the course content to be highly accessible and tailored to non-techies, which made it a perfect match for my needs. The instructors were adept at demystifying complex concepts, making them easy to understand and applicable to everyday situations."
— James Parker ⭐⭐⭐⭐⭐
"The videos are well organized and very thorough. They teach me these topics as if I have no background in the subjects, and I really appreciate that! I feel like I'm really understanding the lessons. Additionally, each video is pretty short and digestible, so I don't feel mentally drained after each lecture."
— Angel Dees ⭐⭐⭐⭐⭐
"Excellent introductory course. It is broad enough to give you a real essential overview of cybersecurity but detailed enough that it's not superficial. Instructor is fantastic - very clear, very easy to understand and has a very pleasant speaking voice which is very nice too. I've done a lot of online self-paced courses and a nice easy to understand instructor helps with your overall learning when you're trying to absorb a lot of complex or (in my case) new content."
— Rosa Cortez ⭐⭐⭐⭐⭐
Section Introduction
FREE PREVIEWThe CIA & DAD Triads
FREE PREVIEWThe Parkerian Hexad
FREE PREVIEWAuthentication, Authorization, and Accounting (AAA)
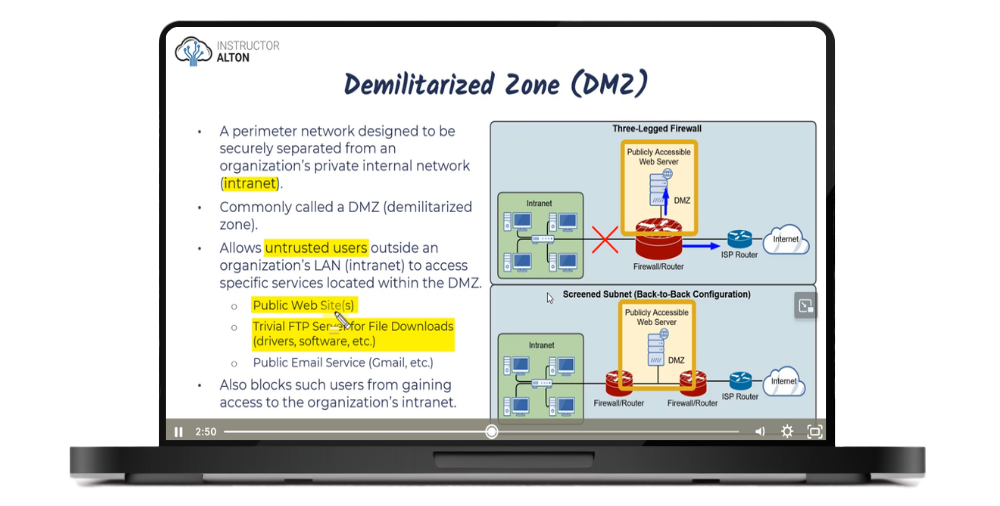
FREE PREVIEWDefense in Depth
Least Privilege
Non-Repudiation
Implicit Deny
Legal and Regulatory Issues
Information Security Governance
Authentication Basics
Identify Proofing
General Password Rules
Modern Password Guidelines
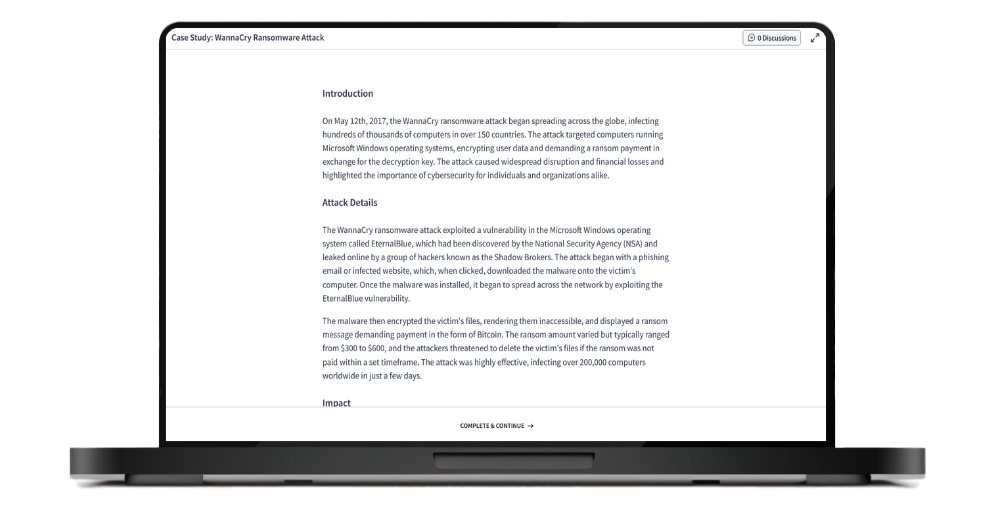
Case Study: Netflix's Calculated Risk for Cloud Success
Student Activity: Netflix Case Study Analysis
Information Security Principles Quiz
Section Introduction
What is a Risk?
What is an Issue?
Introduction to Risk Management
Risk Management Process
Who Uses Risk Management?
The Role of Risk Appetite & Tolerance
Exploring Risks and Threats
Common Risk Categories
Identifying IT Risks
Quantitative Risk Analysis
Attack Surface Analysis
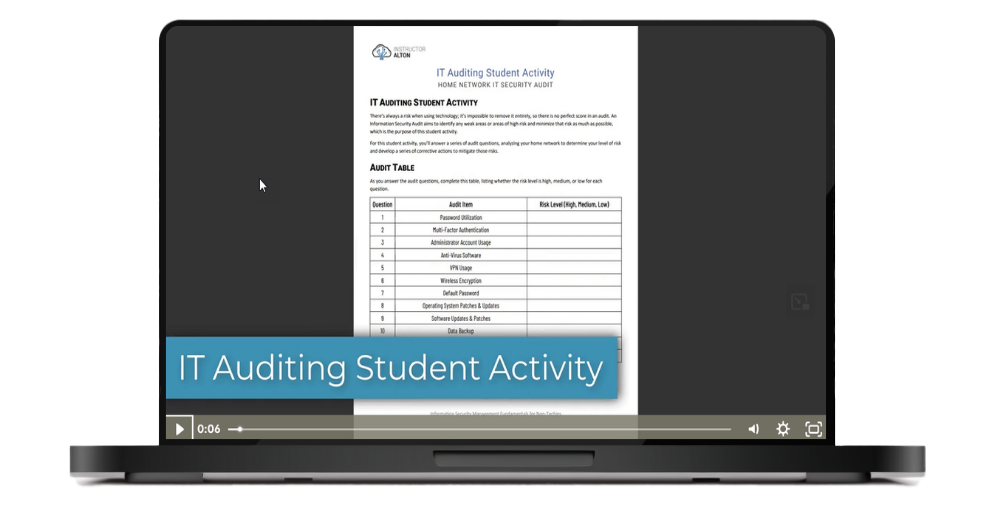
Student Activity: Qualitative Risk Assessment
Risk Management Quiz
Section Introduction
Identifying and Classifying Assets
Emerging Modern Asset Types Reference List
Understanding the Asset Lifecycle
Data Retention
Understanding Data States
Asset Management Quiz
Section Introduction
Access Control
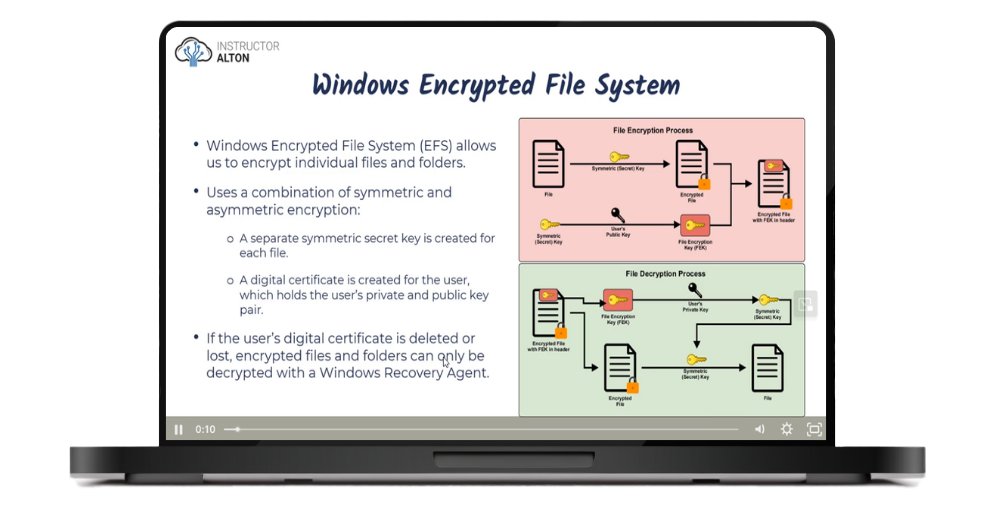
Physical and Logical Access Controls
Access Control Models
Attribute-Based Access Controls (ABAC)
Modern Authentication Methods
Privileged Access Fundamentals
Student Activity: Analyzing Your Organization's Access Control
Access Control Quiz

Alton is the founder of Alton Teaches LLC and a former college professor. He spent 12 years as a cybersecurity specialist at the U.S. Department of the Treasury, working in governance, risk, and compliance. He holds an MBA in Information Assurance and Security Management and multiple certifications, including CISSP, Security+, and Network+.
250,000+ students taught across cybersecurity and IT courses. 90,000+ copies sold of his bestselling books. 19 courses published as a Udemy Instructor Partner with seven best-selling and highest-rated courses.
This course takes a unique approach: it's comprehensive yet accessible, technical yet understandable, thorough yet not overwhelming. Here's what makes it different:
"As a Cybersecurity professional for the DoD, this is a great refresher course for anyone that requires it."
— Eric Trimble ⭐⭐⭐⭐⭐
"I would recommend this course even to experienced IT person as this is the fundamental and in my view cover all of the security. An exceptional well-structured course. After completing this course, I am determined to continue to study/reading on Security for knowledge purposes. This course is definitely going to aid me in my position as Project Manager. Thank so much."
— Harry ⭐⭐⭐⭐⭐
"The break down of the information is very insightful, and the real world example give further root to how the information can be applied. The downloadable resources allow me to print and make my own notes as well."
— Anthony Stewart ⭐⭐⭐⭐⭐
Join 71,500+ students in Udemy's #1 Data and Information Management course. 16.5 hours of comprehensive training with 21 quizzes, 16 activities, 7 case studies, lifetime access, 14-day money-back guarantee.
This course is designed for business owners, managers, aspiring IT professionals, project managers, and anyone who needs to understand cybersecurity from a management and strategic perspective. No technical background required—everything is explained from the ground up.
No. This is not an ethical hacking course, penetration testing boot camp, or network security configuration course. You won't learn how to hack systems or configure firewalls. Instead, you'll gain a comprehensive understanding of information security management principles, frameworks, and best practices—the knowledge you need to make informed security decisions and communicate effectively with technical teams.
No prerequisites required. This course is specifically designed for non-technical professionals. If you can use a computer, you can take this course and understand the material.
The course contains 16.5 hours of video content across 190+ lectures. Most students complete it in 3-6 weeks, but you have lifetime access so you can learn at your own pace. Each video is relatively short (5-15 minutes) so you can fit learning into your schedule.
You get 16.5 hours of video lectures, 21 section quizzes, 16 student activities, 7 case studies, downloadable PDF versions of all slides, closed captions in 14 languages, and lifetime access to all materials including future updates.
This course provides an excellent foundation for understanding cybersecurity concepts and will help you understand what's covered in certifications like Security+, CISSP, or CISM. However, you'll need additional certification-specific study materials to pass those exams. Think of this course as your comprehensive introduction that prepares you to pursue more specialized certifications.
Yes. This course is updated annually with the latest threats, technologies, statistics, and best practices. The 2024 update included current breach costs, ransomware statistics, and emerging threats like AI-powered attacks.
We offer a 100% satisfaction guarantee. If you are unsatisfied with your purchase, you may request a refund within 14 days of the original purchase date.