Cybersecurity for Absolute Beginners: Essential Concepts
Learn the core principles of IT security: networking fundamentals, threat landscapes, defense strategies, and workplace security practices.
The global cost of cybercrime exceeded $10.5 trillion in 2025 and continues to rise. The industry faces a massive skills gap with a shortage of over 4.8 million qualified professionals worldwide. Whether you are an aspiring IT professional or a business owner, understanding the mechanics of digital defense is now an essential life skill.
This course moves beyond theory. We analyze real-world disasters and provide you with reference materials to keep long after you finish the videos.
This course is Part 1 of a comprehensive cybersecurity series designed for absolute beginners. We strip away the jargon and focus on the fundamental concepts used by security professionals every day.
"Such an educational and interesting course. I took this course because I had a mild interest in cybersecurity, but found myself so invested in the topics. Alton is a great teacher, and really makes the concepts understandable."
— Juliana Goyenetche ⭐⭐⭐⭐⭐
"From someone who has little to no basic knowledge of cybersecurity, this was the perfect place to start as it's given me a simple, yet informative understanding on where to go next."
— Christine May ⭐⭐⭐⭐⭐
"The cybersecurity course was excellent. It was easy to follow, very informative, and full of practical examples. The instructor explained everything clearly and made the sessions engaging."
— Alvin Ambri ⭐⭐⭐⭐⭐
Welcome to the Course!
FREE PREVIEWWhy Learn Cyber Security from Me?
FREE PREVIEWCourse Companion Study Guide
Course Case Studies Overview
FREE PREVIEWStudent Exercise: Introduce Yourself
Section Introduction
FREE PREVIEWWhat Hacking Isn’t
FREE PREVIEWTypes of Hackers
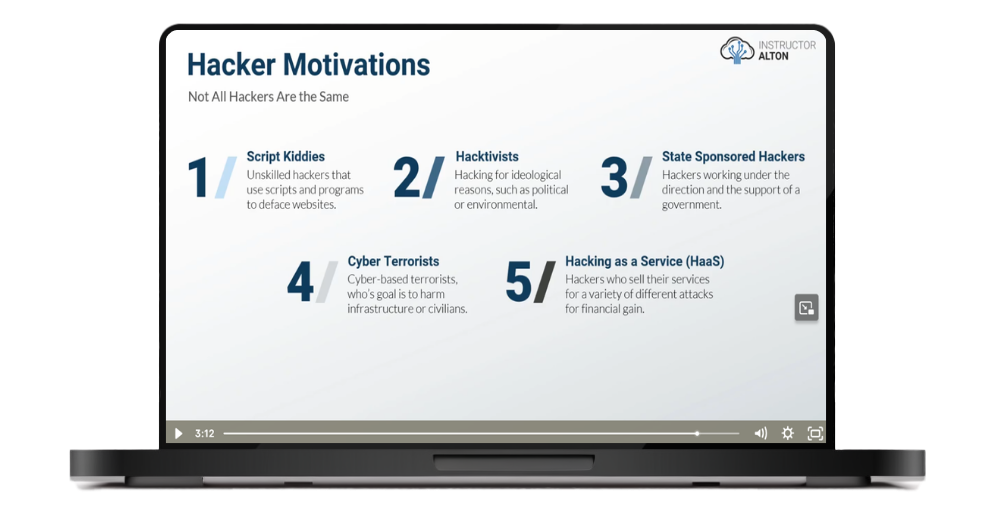
FREE PREVIEWHacker Motivations
The Hacking Methodology
Section Introduction
What is a Computer Network?
Some Basic Networking Rules
Computer Protocols
LANs versus WANs
MAC versus IP Addresses
Switches versus Routers
TCP/IP Protocol Suite
How the Internet Works (Simplified)
Student Exercise: Identifying your MAC and IP Address (Windows and Mac OS)
Section Introduction
Viruses and Worms
Trojan Horses and Logic Bombs
Spyware and Adware
Ransomware and Rootkits
Mobile Malware
How Hackers Deploy Malware
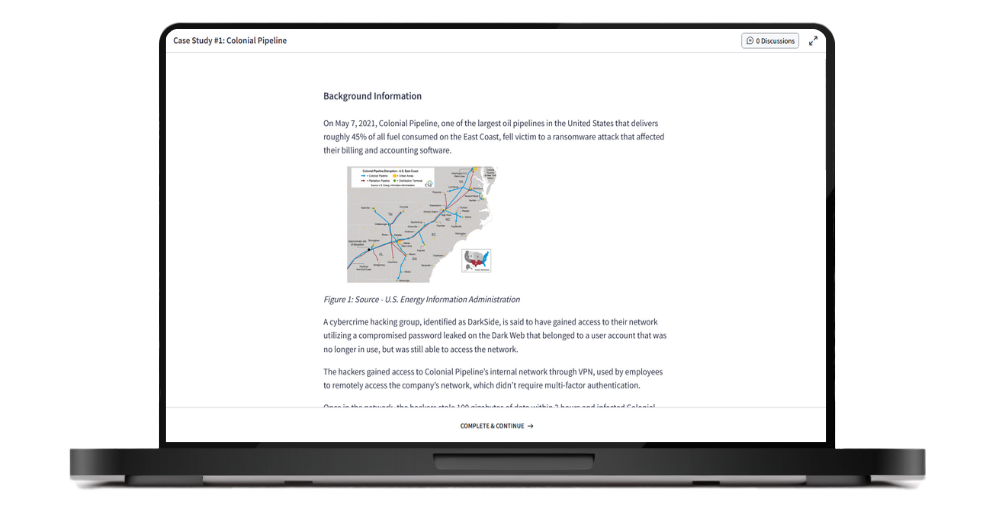
Case Study #1: Colonial Pipeline
Section Introduction
Zero-Day Attacks
Buffer Overflows
Protocol Spoofing
DoS and DDoS Attacks
Weak Encryption & Software Vulnerability Attacks
Web-Based Attacks
Evil Twin and Rogue Access Points
Case Study #2: TJX Companies Inc. (TJX)

Alton is the founder of Alton Teaches LLC and a former college professor. He spent 12 years as a cybersecurity specialist at the U.S. Department of the Treasury, working in governance, risk, and compliance. He holds an MBA in Information Assurance and Security Management and multiple certifications, including CISSP, Security+, and Network+.
250,000+ students taught across cybersecurity and IT courses. 90,000+ copies sold of his bestselling books.
Theory is useless without context. This course breaks down two massive real-world breaches to show you exactly how vulnerabilities are exploited—and how they could have been prevented.
4 hours of expert instruction, real-world case studies, and a comprehensive study guide. Risk-free with our 14-day guarantee.
No. This course is designed for complete beginners. Every concept is explained from scratch with no assumptions about prior knowledge.
The course contains 4 hours of video content. Most students complete it within one week, but you have lifetime access so you can learn at your own pace.
You get 4 hours of video lectures, a 37-page companion study guide (PDF), detailed analysis of 2 real-world case studies (Colonial Pipeline and TJX Companies), and lifetime access to all materials.
Part 1 (this course) covers essential cybersecurity concepts and workplace security. Part 2 focuses on personal online security—protecting yourself on social media, shopping safely online, and securing your home network. Part 3 covers operating system security for Windows, Linux, and Mac. Each course stands alone, but Part 1 provides the best foundation.
We offer a 100% satisfaction guarantee. If you are unsatisfied with your purchase, you may request a refund within 14 days of the original purchase date.